- Remote teams that need a trusted “office IP” for SaaS allowlists
- SMBs replacing legacy VPN appliances
- Compliance-driven access patterns (least privilege, auditability)
Subscribe to GEN
Login to GEN
Managed WireGuard networking with modern identity, device checks, and policy-driven access.
Replace the “flat network” VPN with a service designed for least privilege: secure remote access, predictable egress IPs, and—on the advanced tier—granular routes, ports, groups and posture checks.
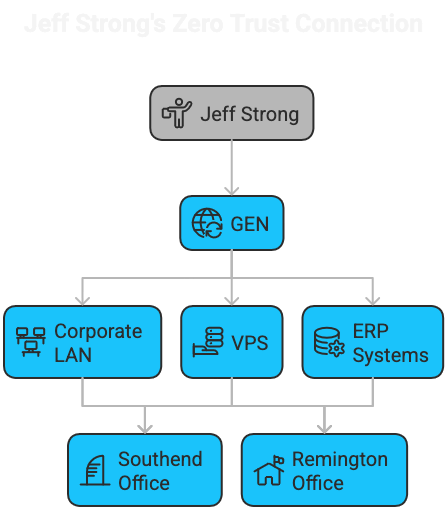
This service is a managed WireGuard network with an identity layer (Zitadel) and a policy layer. Instead of “connect = full network access”, we design access around who the user is, what device they’re on, and what they’re trying to reach.
Good for
Contract
Both tiers
| Tier | Price | Setup | Access & controls |
|---|---|---|---|
|
Secure Gateway Simple tier |
£8 per user / month 12-month contract, billed monthly |
|
|
|
Managed Zero Trust Granular tier |
£15 per user / month 12-month contract, billed monthly |
|
|
Prices are per named user. Larger deployments, additional regions, or complex routing requirements may require a tailored design.
Zero Trust means we don’t assume a device is trusted just because it’s “on the VPN”. Every access decision is treated as a new request to be evaluated.
WireGuard is a modern VPN protocol known for strong cryptography, small attack surface, and excellent performance. It’s a great fit for always-on remote access.
Exit Nodes
An Exit Node is where your VPN traffic leaves the private network and accesses the internet. It’s how remote users appear to come from a known, consistent IP address (your “office IP”).
On the Secure Gateway tier, all users share one high-speed exit. On Managed Zero Trust, you can have multiple exits (e.g. by region, office, or security zone).
Routes
Routes decide which internal networks a user can reach over the VPN—for example a specific subnet containing file servers, a lab network, or a cloud VPC.
Policies & Groups
Policies define what is allowed. Groups keep management simple by applying those policies to a set of users (and optionally devices).
Micro-segmentation (Ports & Protocols)
Instead of “VPN gives you the whole network”, we can allow only the specific ports needed. For example: SSH to a bastion, RDP to a jump host, or HTTPS to an internal app.
Posture checks
Posture checks are rules about the device’s security state—used to allow, restrict, or block access. Typical checks include: OS version, disk encryption, endpoint protection, and device enrolment.
This is where zero trust becomes practical: a user can be valid, but access can still be limited if the device doesn’t meet your baseline.
Want a quote or a quick design call?
Tell us how many users you have, where your apps live (on-prem, cloud, or both), and what you need to protect.